Digital identity is the unique representation of a subject engaged in an online transaction. The global digital identity market is projected to grow at a CAGR of 19.5%. This rapid growth is driven by the digital transformation across sectors such as government, healthcare and finance, coupled with regulatory compliance and evolving data protection standards. While digital identity is unique to specific digital services, accessing these services does not guarantee a connection to the subject’s real-life identity. Authentication over a network poses risks, including impersonation or fraudulent identity claims.
One of the most significant threats to digital identity is identity fraud, which is exacerbated by AI-powered false documentation generation tools like StyleGAN (Style Generative Adversarial Network), which can create highly realistic fake documents, with holograms, microprints and other security features, making conventional verification methods less effective. The National Institute of Standards and Technology (NIST) classifies the assurance of a subject’s identity and authentication strength into Identity Assurance Levels (IAL) and Authenticator Assurance Levels (AAL), explained below:
Assurance level 1
Identity Assurance Level 1 (IAL1): Attributes like name or email address provided by the subject are self-asserted and are neither validated nor verified. There is no requirement to link the applicant to their real-life identity. IAL1 is suitable for applications where impact is low, like entertainment/streaming applications.
Authenticator Assurance Level 1 (AAL1): Provides some assurance that the claimant controls an authenticator tied to their account. It usually involves single-factor authentication.
Assurance level 2
Identity Assurance Level 2 (IAL2): Evidence must support the real-world existence of the claimed identity, verifying that the applicant is appropriately associated with it. IAL2 confirms that individuals have a genuine identity, which can be a photo ID like a driving license, or Aadhar.
Authenticator Assurance Level 2 (AAL2): This level provides high confidence that the claimant controls the authenticator(s). Two distinct authentication factors are required via secure protocols and cryptographic techniques.
Assurance level 3:
Identity Assurance Level 3 (IAL3): Identity attributes must be verified by a trained and certified Credential Service Provider (CSP). IAL3 ensures a highly reliable link between the user's claimed identity and their actual real-world identity.
Authenticator Assurance Level 3 (AAL3): Provides very high confidence in authentication. Claimants must prove possession of two distinct authentication factors, using hardware-based authenticators and methods that resist verifier impersonation. Cryptographic techniques are mandatory.
Verification vs. Authentication
Verification ensures that a person’s claimed identity is valid and trustworthy. It typically occurs at the start of a relationship (e.g., onboarding). It matches the identity against trusted data sources.
Authentication confirms that the individual accessing an account is the same one previously verified. It is a continuous process throughout a user’s journey.
Both processes are critical to identity security. Without stringent verification, systems remain vulnerable to fraud, and weak authentication may compromise legitimate credentials.
The role of identity proofing
Identity proofing ensures that an individual claiming to exist in the real world is genuine. This process prevents fraud, strengthens security and establishes trust in online transactions. By integrating identity proofing, organizations can ensure that only authorized individuals can access sensitive information or services.
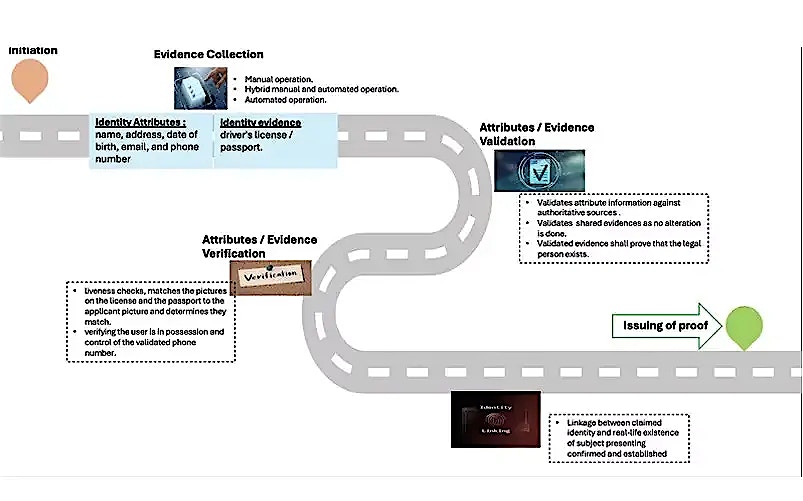
Integrated use-cases
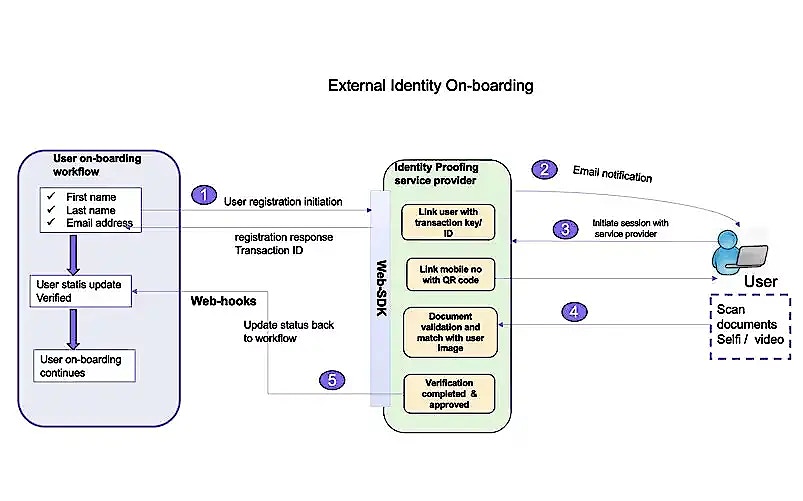
External user onboarding: External user populations, such as vendors, suppliers, partners or contractors, often pose higher security risks during onboarding. The Identity Governance and Administration (IGA) workflow can integrate identity proofing to validate these users:
- During onboarding, IGA workflow calls the Identity proofing service provider's API with basic information (e.g., username, email, phone number).
- The user receives a session link to upload required documents and selfie/liveness verification.
- User initiates session and provides documents for verification.
- The proofing service validates the user and confirms identity status.
- Onboarding continues, granting credentials and access to IT systems.
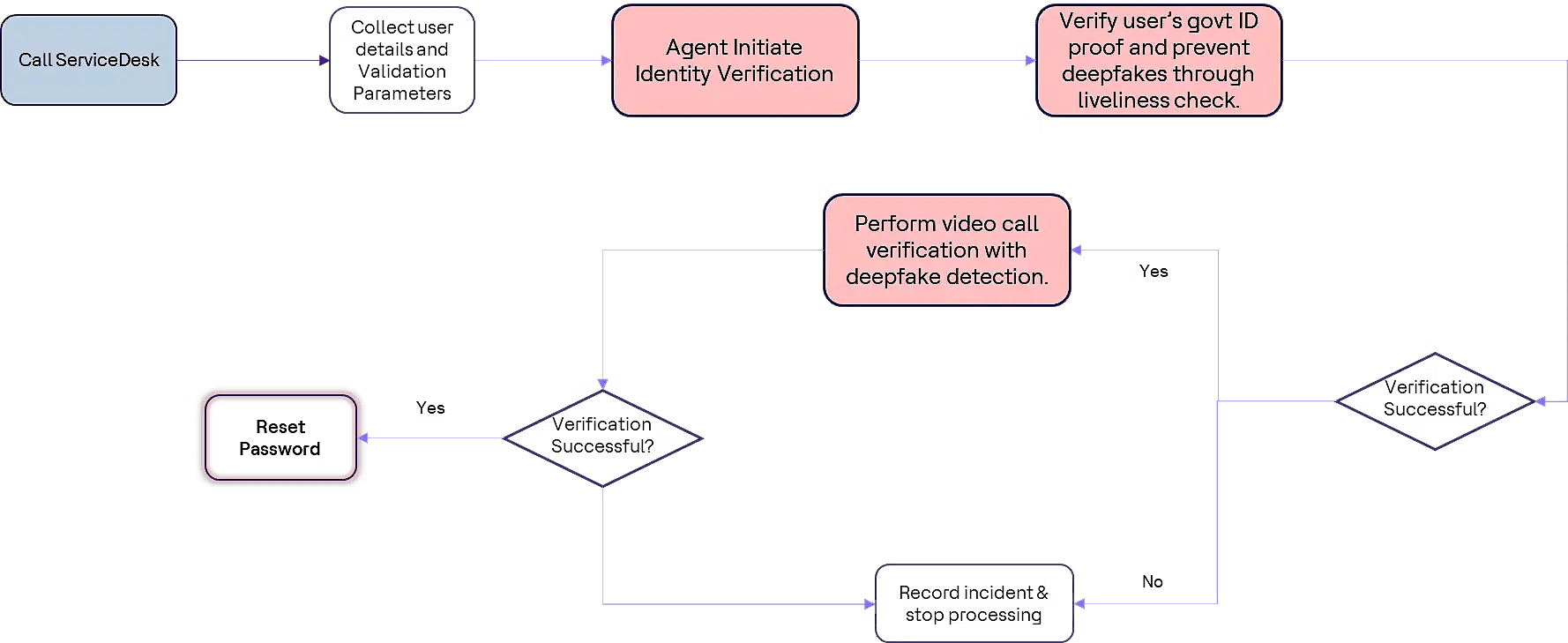
Password reset calls, protecting against social engineering attacks: Service desks are vulnerable to social engineering, as basic user details (e.g., from social media) can be used to impersonate individuals. A robust identity verification process during reset calls can prevent unauthorized access:
- The user scans their government-issued ID and uploads it.
- The identity proofing solution verifies the ID by integrating with government services.
- Alternatively, a video call with a service desk representative can help confirm the user’s identity using liveness checks and deepfake detection.
- Upon successful verification, the password is reset, and secure communication is established.
Conclusion
With increasing identity-related fraud and attacks, identity verification and authentication are foundational to building trust in digital ecosystems. Organizations must adopt advanced identity proofing measures, integrate them with their workflows (e.g., via APIs) and ensure compliance with industry standards like those outlined by NIST. Such steps can mitigate risks, protect sensitive systems and enable a safer digital environment.
HCLTech plays a key role in advancing digital identity solutions by helping organizations implement robust identity verification processes, integrate Identity Governance workflows and strengthen authentication mechanisms using AI-powered tools and cryptographic protocols. By providing tailored digital identity solutions, HCLTech enables businesses to address regulatory requirements, combat fraud and ensure secure user journeys across digital platforms.


