There is no doubt that organizations are investing loads of money in information security recently due to increased incidences of data breaches and expectations from crucial clients. It has now become a requirement for doing business. Unlike in the past, more and more organizations are now increasing their dependence on third parties for providing goods and services to their clients. This is due to the following reasons:
- Focusing internal workforce on core business processes which saves money and provides better return on investments
- Acquiring a niche skill that an organization might not have in-house, to achieve certain business objectives
- Acquiring a basic utility service that cannot be efficiently provided by the organization (such as power)
But as everything has its pros and cons, the downside of utilizing third party vendors is that the organization must expose or provide access to their information systems that host and process critical data, to third parties. Managing an organization’s own risk profile has never been this difficult. Another concern of the top executives is how well is every third-party vendor managing their own security posture. If unsafe, it could directly or in-directly impact the core organization in terms of financial, reputational, compliance and regulatory risks and exposure.
Information security risks involving third-party
Organizations and their third parties can cause information security risks to each other. Some of these risks are explained below:
- Organization’s dependence on third parties complicates their own business continuity and resiliency arrangements
- Shared responsibilities between an organization and third parties defeats the zero-trust model
- Understanding complex coordination between an organization and third parties to adapt and respond to legal/regulatory changes
- Mismatch between organizational and third-party policies, in terms of maturity
- And many more.
What is ISO 27036 and how does it help manage complex third-party relationships?
ISO 27036 comes from the family of ISO 27000 series of standards which provides a framework for improving practices when developing Information Security Management Systems (ISMS). ISO 27036 provides guidance on how to manage information security related risks when acquiring goods and services from a third-party. The standard uses terms like ‘acquirer’ and ‘supplier’ rather than the organization and third party.
Scope and application of ISO 27036
The standard applies to commercial relationships between an acquirer and supplier for providing goods and services, such as:
- Supply of hardware, software and information and communications technology (ICT)
- Cloud computing services
- Support services such as housekeeping and security guards
- Public services such as power, water, etc.
ISO 27036 architecture
ISO 27036 is a multi-part standard. The figure below provides the notional architecture of the standard:
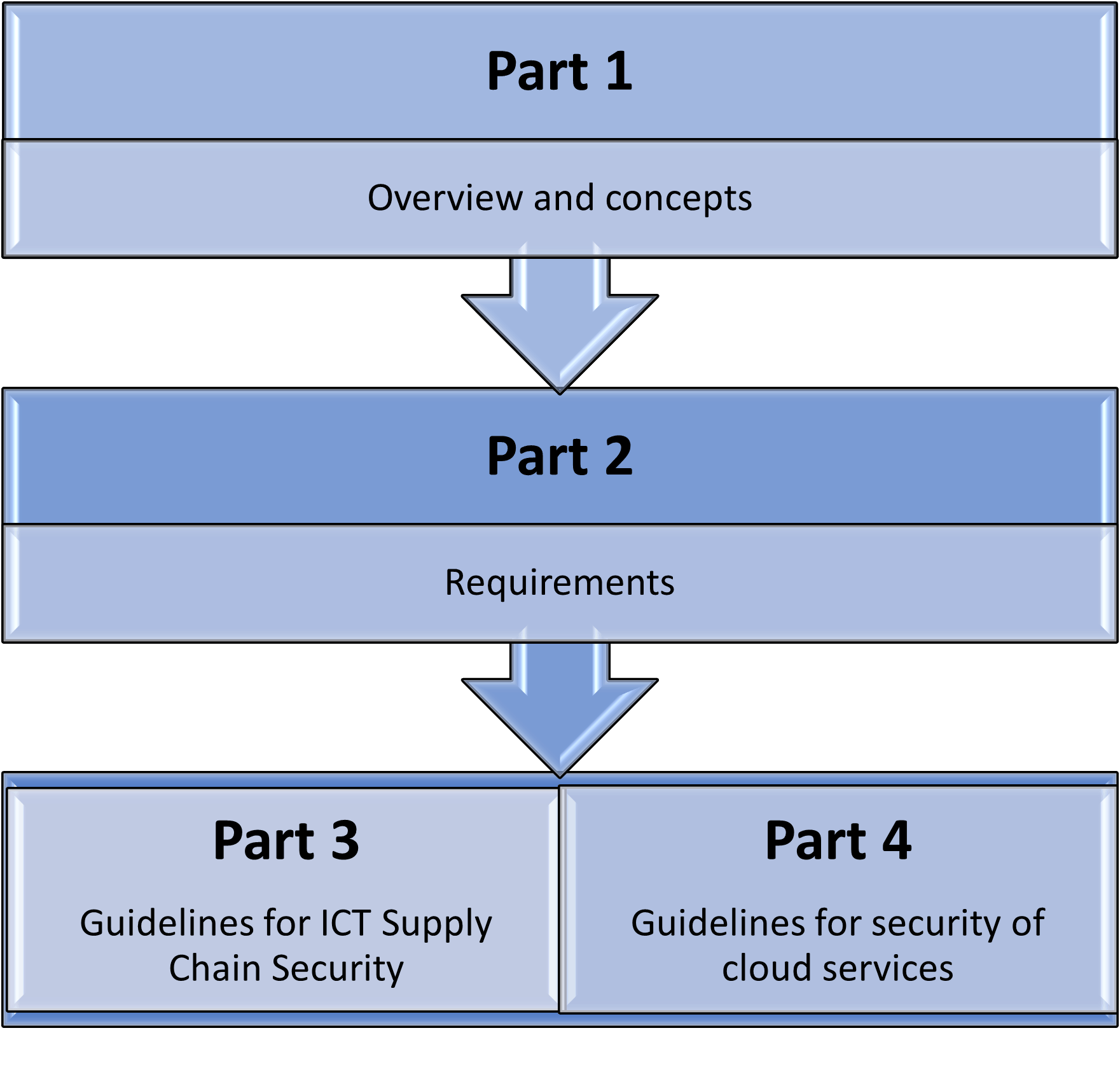
Fig 1: ISO 27036 Architecture
Part 1: ISO 27036-1:2021 - Overview and concepts
Part 1 is the introductory part of ISO 27036 which intends to support an acquirer in securing their information systems within the context of supplier relationships. It also introduces key terms and concepts along with risks relating to information security for supplier relationships.
Part 2: ISO 27036-2:2022 - Requirements
Part 2 states information security requirements for defining, implementing, managing, monitoring, reviewing, sustaining, and enhancing acquirer and supplier relationships. These requirements are generic in nature and can be applied across any procurement or supply of goods and services relationship between acquirer and supplier. Despite having “Requirements” in the title, it is not intended for certification purposes. Clauses 6 and 7 define the requirements and are consolidated in Annexure C of the standard. To meet these requirements the organization is expected to have internally implemented support functions such as a robust business management function, risk management function, operational and human resources management and information security management systems.
Part 3: ISO 27036-3:2013 - Guidelines for information and communications technology (ICT) supply chain security
Part 3 assists acquirers and suppliers involved in providing goods and services within the information and communications technology (ICT) sector, around information security risks and their management, relating to the use of complex supply chains. It covers a wide range of information security controls such as:
- Chain of custody
- Least privilege access
- Separation of duties
- Compliance management
- ICT supply chain security training
- Ownership and responsibilities
- Avoidance of gray-market components
Part 4: ISO 27036-4:2016- Guidelines for security of cloud services
Part 4 provides guidance on information security to customers of cloud services and cloud service providers. It also speaks to how to effectively manage risks for public, hybrid, and private cloud deployment models, by implementing specific controls to mitigate these.
Lifecycle of ISO 27036
The figure below depicts different phases of the supplier relationship:
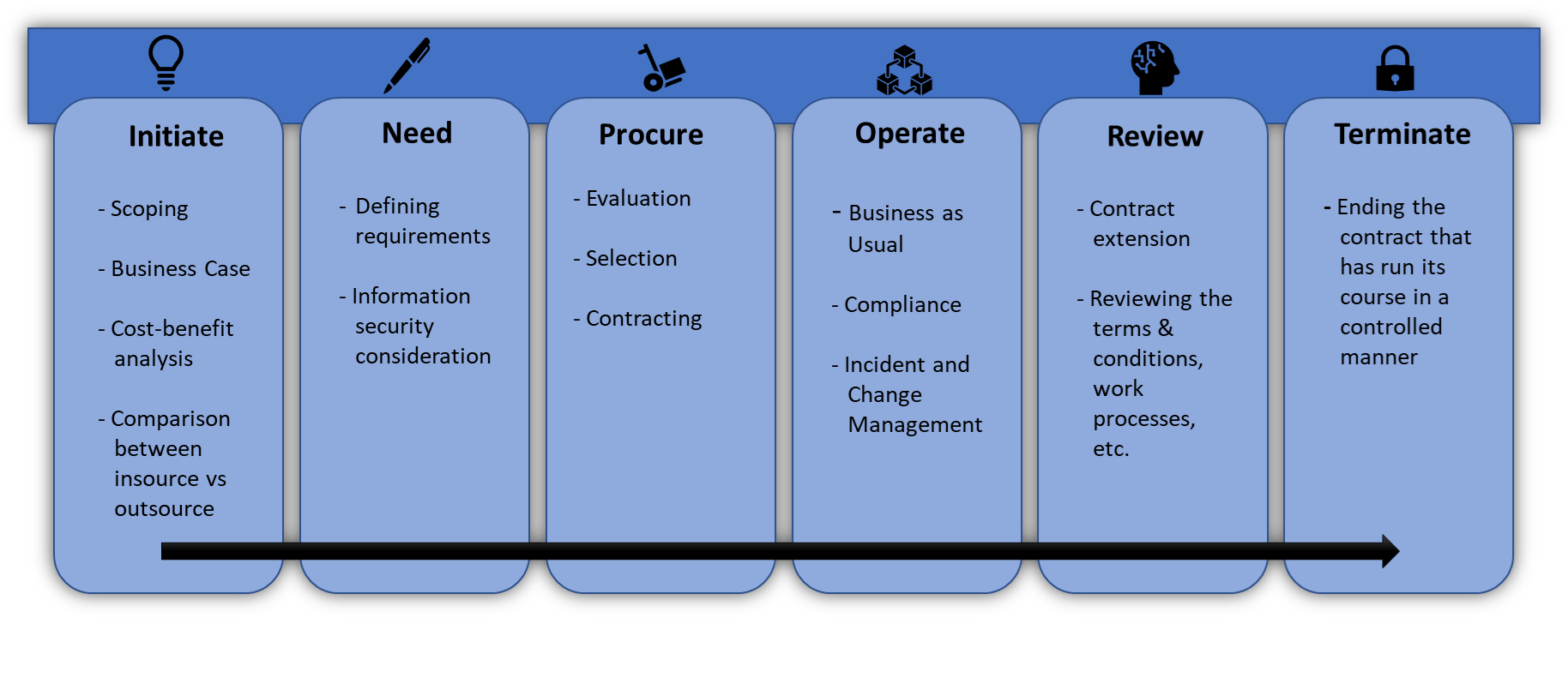
Fig 2: ISO 27036 Lifecycle
Initiate
During the initiate phase, the scoping of goods and services to be outsourced is performed, a comparison is done between insource versus outsource options and then a cost-benefit analysis is performed for each option.
Need
Requirements from the relationship are identified along with the information security considerations.
Procure
Different parties providing the required services are analyzed and the selection and contracting are done after careful evaluation.
Operate
It consists of business-as-usual activities along with compliance management.
Review
This is an optional stage where once the initial term of contract has expired and if the relationship is to be extended, then a review is performed of terms and conditions along with work processes etc.
Terminate
This is final phase of the relationship which denotes the end of the relationship that has run its course in a controlled manner.
Key takeaways from ISO 27036
Parts 3 and 4 of the standards, highlight the guidelines for information and communications technology (ICT) supply chain security and security of cloud services, respectively. Below are some key information security considerations, to help manage a robust supplier relationship:
- Before entering a commercial relationship, a proper analysis is to be performed by preparing a sound business case and considering the risks, controls, costs, and advantages associated with sustaining adequate information security.
- Creation of shared strategic goals to align the acquirer and supplier on aspects such as information security, etc.
- Stipulating that the suppliers comply with ISO 27001 standard within the master services agreement.
- The relationship must be governed by robust operational management, risk management and incident management procedures.
- Clearly defining roles and responsibilities in terms of operations and security between acquirer and supplier.
- Inclusion of a “Right to audit” clause within the master services agreement and specifying sanctions or liabilities in the event of non-compliance.
The standard comprises professional risks such as security personnel, equipment servicing, cleaning crew, delivery services, and further standard processes concerning the use of “cloud services, data domiciles, shared compliance processes, and other requests”. It could also be unified with ISO 27001 standards and the acquirer’s policies and processes which would offer a holistic framework.



