In today's digital world, ensuring the authenticity of software is more critical than ever. With cyber threats evolving rapidly, how do we know that the applications we download haven't been tampered with? That's where code signing comes in—a security mechanism that helps verify that software is genuine and hasn't been altered since the developer signed it.
But just having code signing certificates isn't enough. If not managed properly, these certificates can fall into the wrong hands and be misused by attackers to sign malware, leading to supply chain attacks and massive security breaches. To prevent this, the CA/Browser Forum (CA/B Forum) has stepped in with strict industry standards for issuing and managing code signing certificates.
What is code signing and why does it matter?
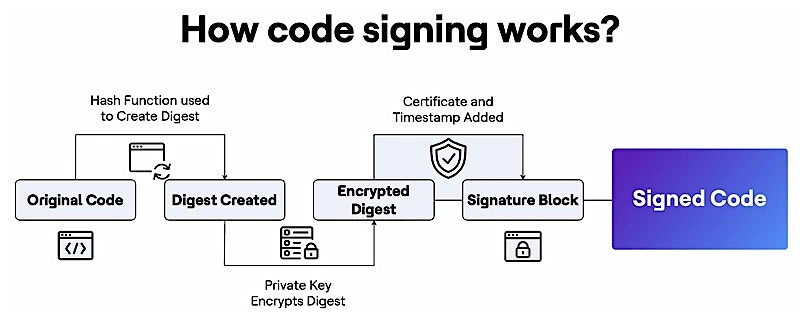
Code signing is like a digital "seal of approval" for software. It uses cryptographic techniques to prove that an application or executable comes from a trusted source and hasn't been modified after signing. When you install software on Windows or macOS and see a pop-up saying, "This app is from a verified developer," that's code signing at work. Without it, there's no way to confirm whether a software update is legitimate or if a hacker has injected malware into it. Attackers often steal or misuse weakly protected code signing certificates to make their malware look like trusted software, which is why securing these certificates is just as important as using them.
Who is the CA/B Forum and why should you care?
The CA/B Forum is a group of Certificate Authorities (CAs), browser vendors (such as Microsoft, Google and Mozilla) and other cybersecurity stakeholders that define the best practices for issuing and managing digital certificates.
They set the rules CAs must follow to ensure that SSL/TLS, S/MIME and code signing certificates are issued securely and cannot be easily misused. Their baseline requirements for code signing outline strict policies to prevent certificate abuse and improve software security. In an era of rising malware and supply chain attacks, code signing certificates are vital in securing software distribution. The CA/B Forum has set strict baseline requirements to ensure the integrity of code signing certificates and prevent abuse.
The need for stronger code signing practices
Code signing is a critical security control that allows users to verify software authenticity. However, cybercriminals often misuse stolen or weakly protected certificates to sign malware. CA/B Forum’s Baseline Requirements v3.9 aims to mitigate these risks with stricter issuance, storage and revocation policies.
No more weak identity checks; stronger verification is a must
Before issuing a code signing certificate, CAs must strictly verify the requester's identity. This includes:
- Confirming the legal existence of a company or individual.
- Validating domain ownership for the certificate.
- Checking government-issued ID documents.
This helps prevent fraudsters from getting valid certificates that they could use to sign malware.
Say goodbye to easily stolen keys; secure storage is mandatory
Private key theft is one of the most significant security risks in code signing. If a private key falls into the wrong hands, an attacker can use it to sign malicious software as if it were from a trusted developer. To prevent this, the CA/B Forum now requires that private keys be generated, stored and used within a certified hardware crypto module that meets FIPS 140-2 Level 2 or Common Criteria EAL 4+ standard guidelines for -
- Hardware Security Modules (HSMs) for on-premises security.
- Trusted Platform Modules (TPMs) for endpoint security.
- Cloud-based Key Management Systems (KMS) for cloud-based signing.
Following these standards means that developers can no longer store private keys in insecure software formats like PFX files, which are easy targets for hackers.
Shorter certificate lifespans and revocation policies
Previously, code signing certificates could last for up to five years. While that was convenient, it also meant that if a certificate was stolen or misused, attackers could continue using it for years before it expired.
To limit this risk, the CA/B Forum has reduced the maximum validity to 39 months. This ensures that companies undergo frequent identity revalidation, making it harder for stolen certificates to stay active for long periods.
Faster revocation: If a certificate is found to be compromised or used for malware, the CA must revoke it immediately, sometimes within 24 hours for high-risk cases. This ensures that compromised certificates are not continued to be used for attacks.
Additionally, CAs must now:
- Use Certificate Transparency (CT) logs to track issued certificates.
- Scan software for malware before issuing a certificate.
This helps detect suspicious activity early and prevents rogue actors from abusing code signing certificates.
Timestamping: Extending trust beyond expiration
Software signed with a code signing certificate can become invalid once the certificate expires. To address this, the CA/B Forum mandates using RFC 3161-compliant timestamps, ensuring signed software remains trusted even after the certificate expiry.
Malware scanning before issuance
A game-changing addition is malware scanning before certificate issuance. This prevents rogue developers from obtaining valid code signing certificates for distributing malware, which significantly reduces supply chain risks.
Final thoughts: A step towards a safer software ecosystem
The CA/B Forum's updated baseline requirements are a massive step toward a safer and more trustworthy software ecosystem. By enforcing strong identity verification, secure key storage, strict revocation policies and mandatory timestamping, the new guidelines make it much harder for attackers to misuse code signing certificates. For developers and enterprises, this means:
- Greater trust in signed software.
- Reduced risk of certificate theft and misuse.
- A stronger defense against malware and supply chain attacks.
In a world where digital threats continue to grow, these measures help ensure that software remains secure, verified and tamper-proof.


