What are multitenancy and keycloak multitenancy?
In multitenant applications, a single software instance can serve multiple tenants (users) or organizations. Each user’s data is isolated and cannot be accessed by others on the same software instance. Multitenancy maximizes resource sharing, allows multiple tenants to log in, and use a single server or cluster. This architecture allows multiple related tenants to share some resources, possibly database, application instances, or infrastructure such as compute, memory, or storage. So, each user gets its own logical instance of the application. Also, some users have the ability to customize some parts of the business application like UI theme. Of course, it's important to manage user identities in this scenario, making an effective identity and access management solution critical.
So, the multitenant application can serve multiple customers. Each customer gets an experience similar to what they would’ve got if the application was custom-built for them. The team building and hosting the application save money and support because of shared resources. In addition, it also secures one tenant’s private data from the other.
To explain multi-tenancy in the real-world scenario, let’s take an example of an office premise with its centralized security system at the main entrance. You get in the office space from the main entrance using your access card. And then get in the office tower with the tower access card. You cannot get in other office towers as you don’t have access to those. You can access your tower’s meeting rooms and café/ break out area. But all the people in the office premises have some kind of shared infrastructure.
- Access security: Tenants are not able to access other domains. Each tenant functions in a separate domain and cannot access the data of any other tenant.
- Less scaling implications: As each user gets its own logical instance, scaling has fewer implications leading to a reduction in costs. In a single-tenant environment, each user or tenant gets own instance of the application.
- Fewer resources needed: With a single instance, the resources such as CPU, database, any persistent volume setup (if running with Kubernetes), etc., are duplicated. The cost may increase depending on your required setup. With Multi-tenancy, only one instance of the application runs with shared resources for related users.
- Performance isolation: Performance impact of one tenant does not impact another tenant.
- Configuration isolation: Each tenant can handle its own isolated domain configuration without affecting the other tenant’s configuration.
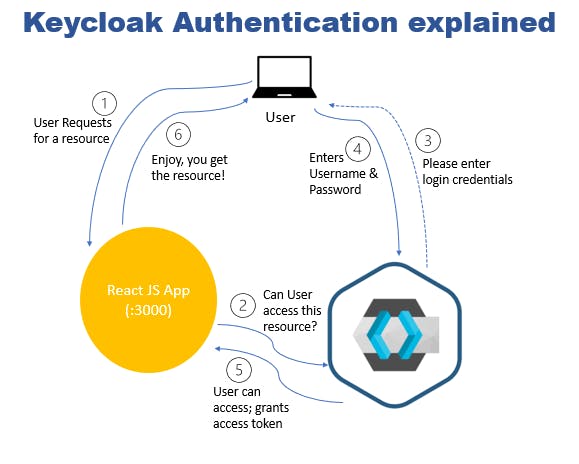
Keycloak authentication flow:
- The user loads the React App and requests access to a resource. A resource is an object being protected. It can be APIs, any data files, statistics data, or certain application pages.
- React App forwards the request to the Keycloak server.
- Keycloak requests the user to enter their username and password to access the protected resource.
- User keys in their username and password and clicks Login on the Keycloak page. This way, the app never sees the user’s password.
- Keycloak authenticates the user with the provided credentials and creates an access token. Keycloak redirects back to the React App with the access token. The app will then use this access token to make any further requests to access.
- React App gives the user access to the requested resource on the keycloak server.
Keycloak multitenancy introduction
Keycloak is an open source identity and access management solution for modern applications and services. It secures applications and services with little or no code at all.
Keycloak multitenancy supports multiple realms. Each realm can have multiple users and clients. Each user from particular realm talks to a client application configured as a client within a realm for authentication.
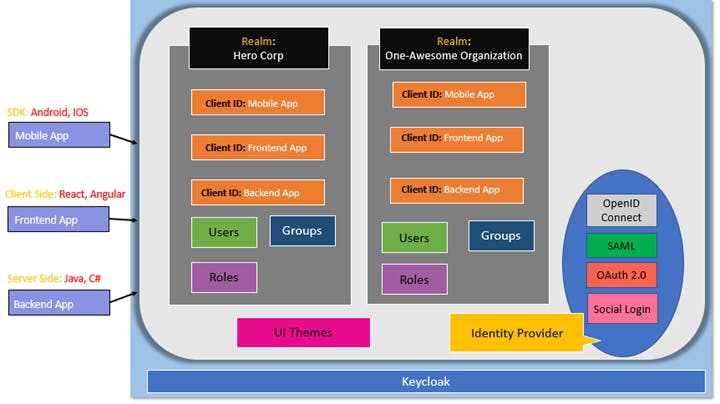
You can integrate mobile Apps, front-end, and backend apps with Keycloak. Keycloak provides a single sign-on solution to organizations. Multiple domains can be created using realms. Realm is like a namespace that allows the managing of the entire domain configuration. As shown above, each realm can be configured to have multiple clients based on the applications that the domain uses to authenticate using Keycloak.
Each realm can have Users, Groups, and Roles. We can customize the UI or theme for Keycloak so that different domains can have different look and feel. Keycloak also provides support for multiple identity providers such as OpenID Connect, SAML, OAuth2, and Social logins such as Google, Facebook, etc.
How Does It Work?
Keycloak supports the OAuth2 authentication flows. One such OAuth2 authentication flow is explained below:
Workflow of keycloak resource owner password credentials grant:
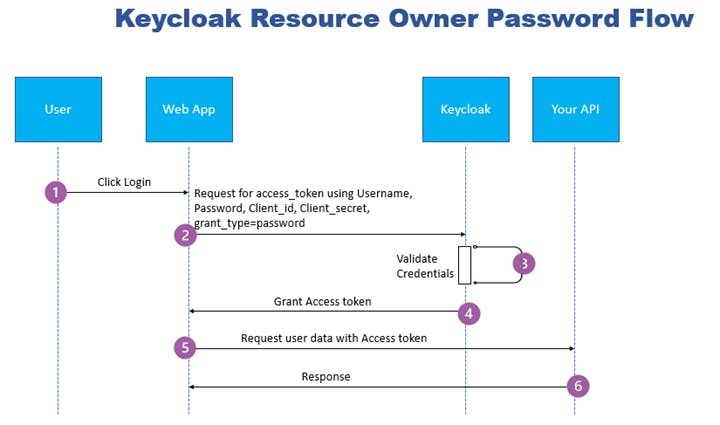
- In the authentication flow, the user clicks login on the client Web application.
- Web application checks for an access token; if not found, the application forwards the user’s credentials to Keycloak token endpoint.
- Keycloak validates the user’s credentials and generates an access token.
- Keycloak server responds with the access token and a refresh token (optional).
- The application can now access the API with this access token to access other protected information.
- The API then re-validates the access token for expiration and valid signature and responds with the requested resource to the end-user, closing the oath2 authentication flow.
Keycloak also supports other OAuth2 authentication flows: Client Credentials Flow, Authorization Code Flow, Authorization Code flow with PKCE (Proof Key for Code Exchange), and Implicit Flow.


