Accelerate Your Digital Transformation
We help businesses adopt digital technologies at the core of business transformation, which includes a combination of core infrastructure services and next-generation digital services that pivot around hybrid cloud, digital workplace, software-defined networking, cybersecurity, unified service management and intelligent operations. Our clients leverage these services to develop long-term digital transformation strategies to meet their current and future needs.

We think these topics might interest you
IT Infrastructure Solutions to Maximize Value for Long-term Success
HCLTech's suite of cloud & infrastructure managed services spans management, hosting, migration, and evolution of your infrastructure, catering to both on-premises and cloud environments.

Hybrid Cloud Services
Our next-generation data centers with autonomics and orchestration capabilities aid in creating unified experiences.

Digital Workplace Services
Our digital workplace strategy, solutions and services bring together technology, people and culture to build a workplace that boosts productivity, engagement and positivity.

NextGen Networks
We enable business transformation and strategic alignment of next-gen enterprise networks, making them lean, agile, experience-centric and outcome-based.

Fluid Contact Center (FluidCC)
FluidCC offers comprehensive technology services and accelerators for contact center digital transformation and assists enterprises in re-imagining their customer service experience by creating AI-powered customer journeys.

Cybersecurity
We help companies Identify, understand and manage security, risks and compliance.

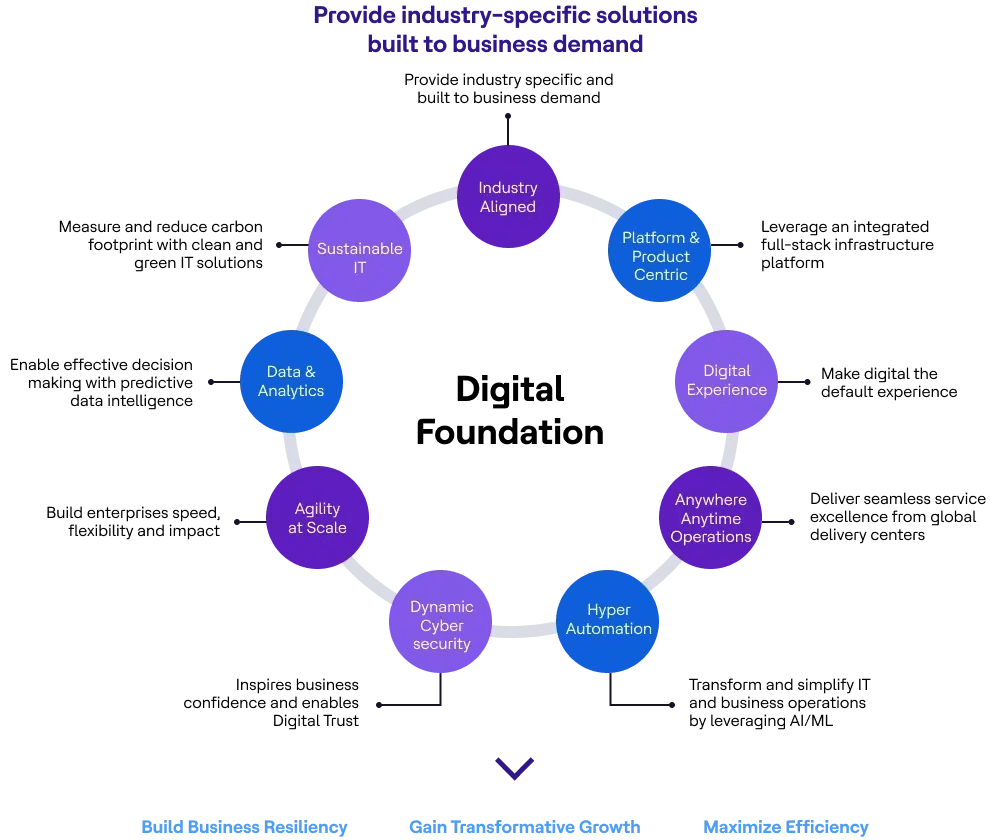
Digital Foundation Consulting
We enable organizations benefit from the right technologies with our approach to digital solutions, people and processes that come together – transforming them into resilient and adaptive enterprises.

Service Integration & Management
We design and build the right SIAM model using our accelerators while implementing and integrating multiple vendors.

Autonomics Services
Transforming IT with NoOps powered by HCLTech Intelligent Operations Platform which is AI-first full stack integrated offering aimed at organizations that require an infusion of advanced AIOps to boost their operations ecosystem.

Infrastructure Modernization Services
End to end AI powered IT modernization services to drive business agility
Digital Infrastructure Solutions to Make Your Enterprise Thrive
Empower your enterprise with our range of cutting-edge digital infrastructure solutions. From optimizing cloud environments to enhancing network reliability and security, we offer comprehensive solutions to drive your business forward.
Client Testimonials
Allied Irish Bank
CIO
"HCLTech drove a very significant project as well as delivering next-gen workplace services in terms of supporting our users."

ArcelorMittal
Head of Corporate
& Transversal Infrastructure
"I was impressed with the capability of a company like HCLTech to adapt and to be able to answer to our needs. Cloud was one of the exciting strategic projects that I had a chance to drive together with HCLTech."